Security Architecture for Professional Services
Designed for firms with the highest confidentiality requirements
Complete Data Isolation
Deploy on your internal network with no external connectivity. All data stays within your security perimeter. No cloud services, no external APIs, no internet access required. Perfect for law firms, healthcare providers, and financial advisors.
Zero Third-Party Access
No vendor access to your deployment. No support backdoors. No telemetry or analytics sent anywhere. Your IT team has complete control. Audit the open source code yourself to verify security claims.
Client Audit Ready
Demonstrate technical controls to demanding clients. Architecture diagrams included. Data flow documentation provided. Open source allows client security teams to review code. Passes third-party security questionnaires.
Reviewer Anonymity Guaranteed
Technical architecture prevents identity tracking. Token-based access with no authentication logs. Configurable minimum response thresholds. Protects both reviewers and reviewees in sensitive firm environments.
Compliance Documentation
Includes templates for ISO 27001, SOC 2, and GDPR documentation. Security control descriptions ready for compliance frameworks. Data processing documentation for client audits. Privacy impact assessment materials provided.
Internal SMTP Only
Configure with your internal mail server. No external email services required. All email stays within your network. Support for Exchange, Office 365 on-premises, or any SMTP server you control.
Secure, Professional Interface
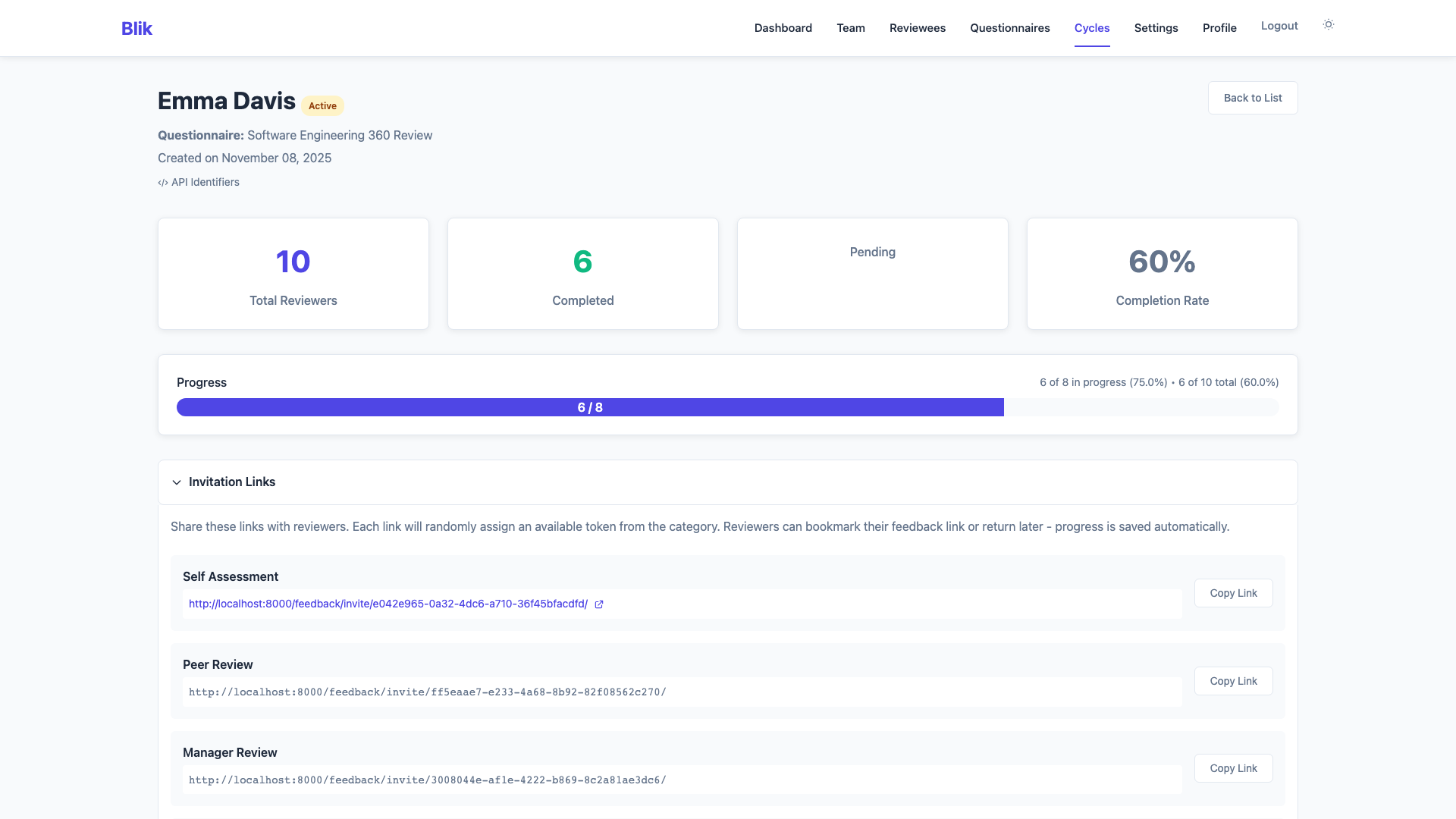
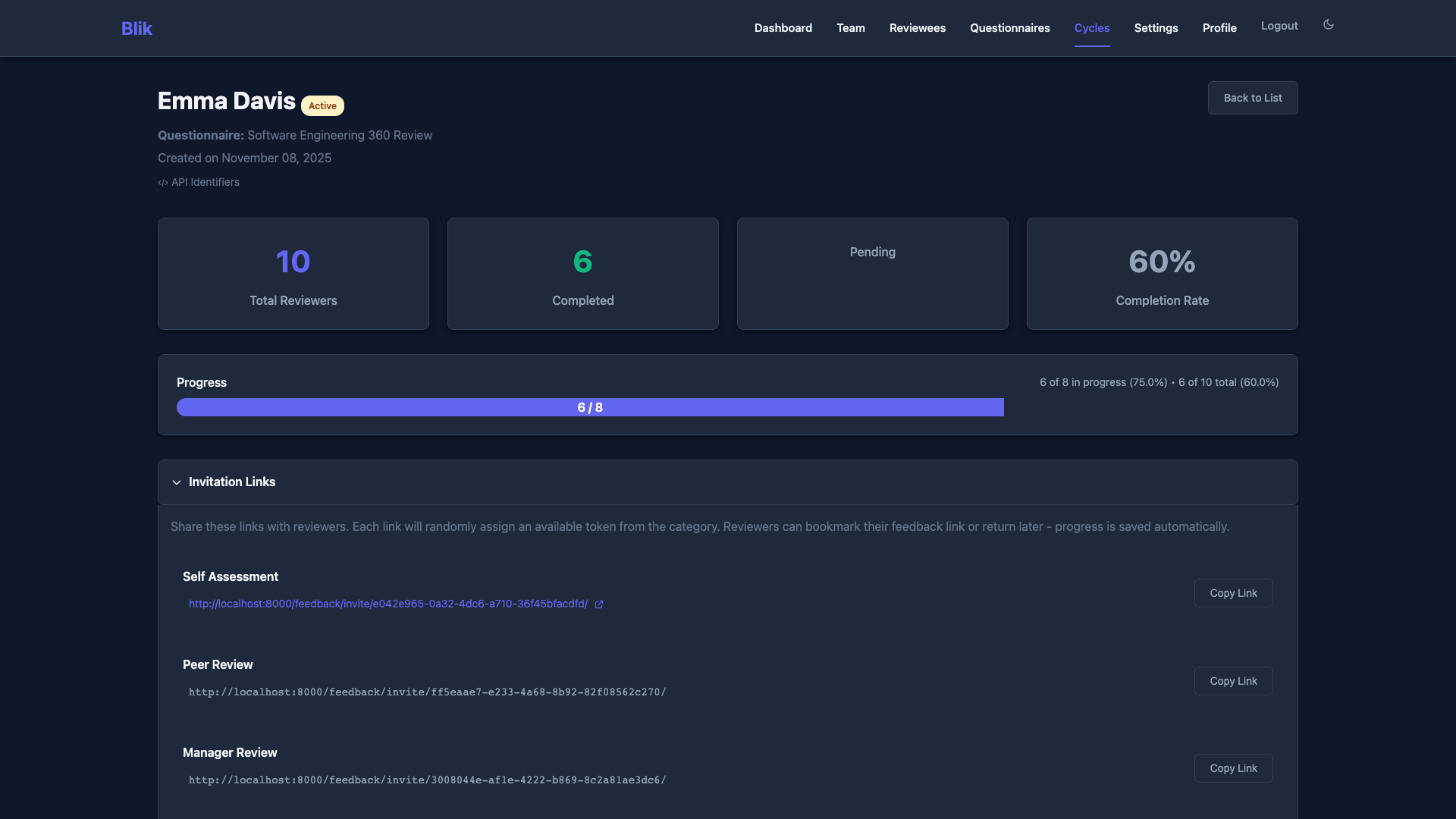
Anonymous invitation links ensure reviewer identities are never tracked or stored
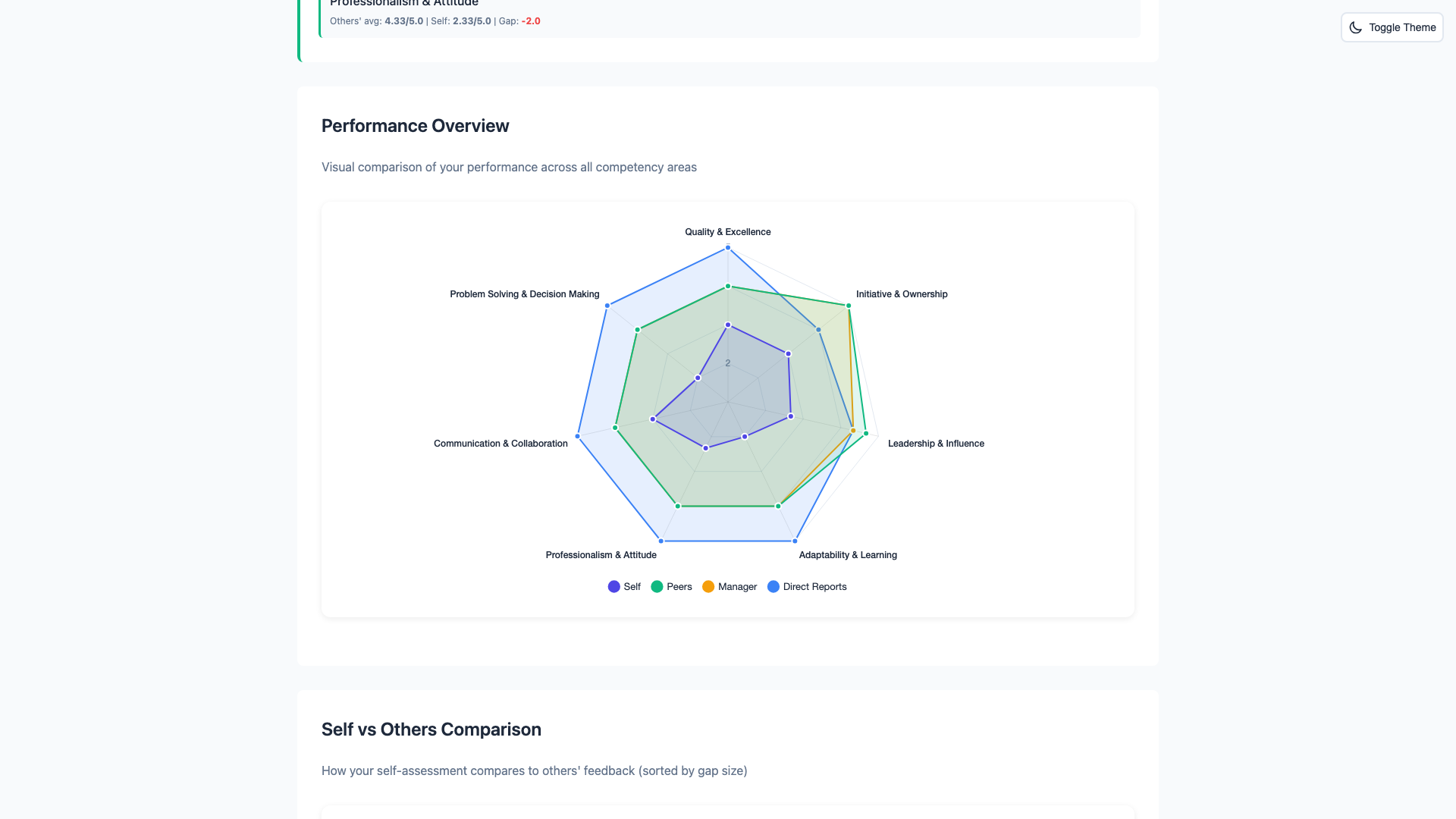
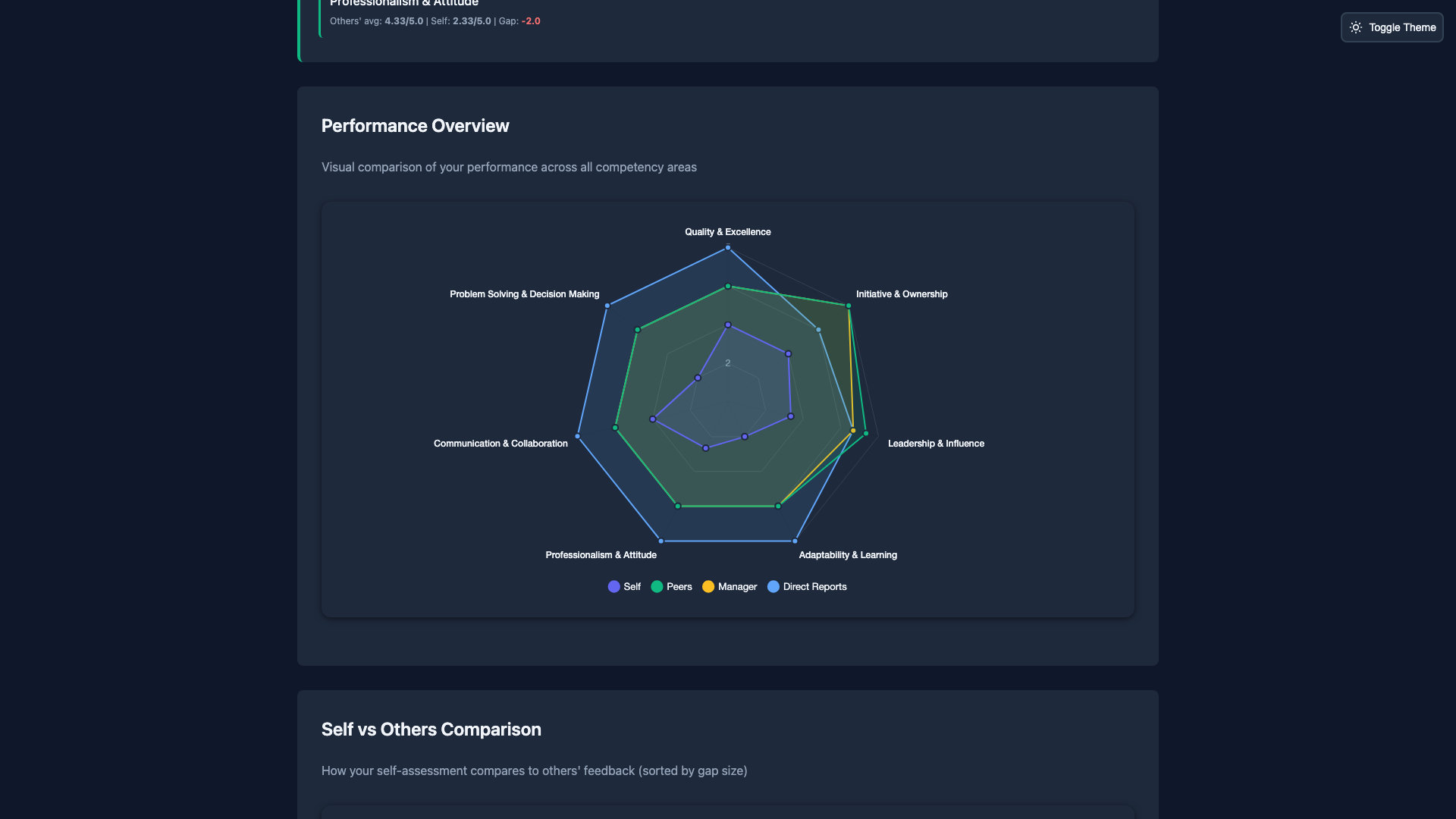
Professional reports with anonymity protection built-in